Cyber Security Management
Cyber Security Management Strategy and Framework
Cyber Security Risk Management Framework
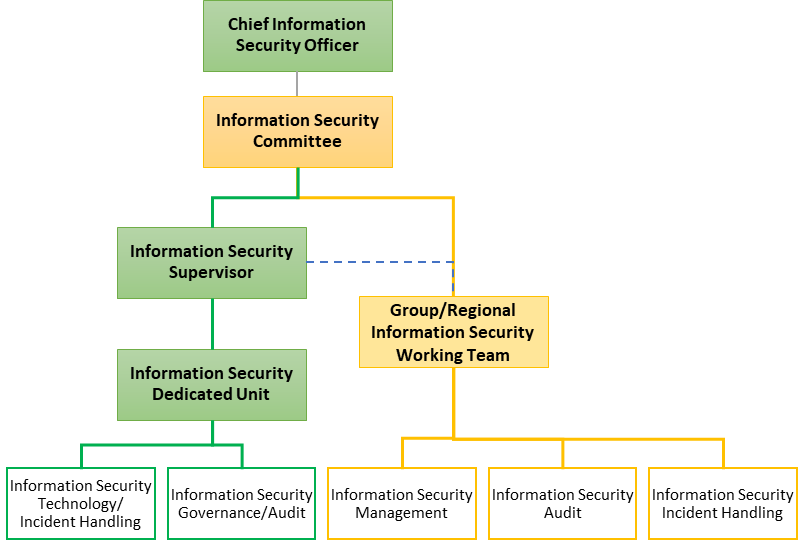
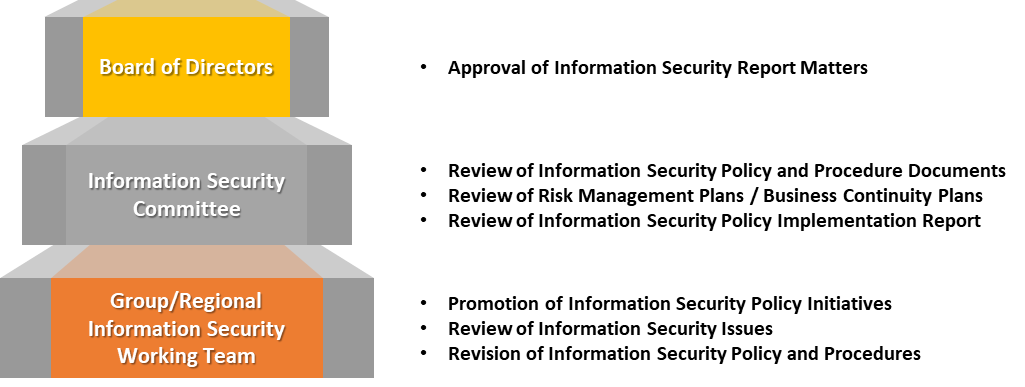
Pou Chen Corporation has appointed a chief information security officer and an information security supervisor, and established an information security dedicated unit since 2022. The head of the Information Department serves as the chief information security officer, convening senior management to establish the Information Security Committee to support, supervise, and make decisions regarding the information security management system. Additionally, an Information Security Working Team is composed of the information security supervisor, information security specialists, and dedicated personnel from various units of the Information Department. This Team is responsible for driving information security governance, technology, incident handling, and audit.
Cyber Security Policy
- 1. Cyber Security Policy and Objectives
The Company has adopted the Information Security Management System (ISMS), in accordance with the international ISO 27001 standard to prepare appropriate documents and control measures for information security system. The purpose of the cyber security policy is to protect the continuous operation environment of information services and information assets from internal and external intentional or accidental destruction. This aims to ensure that relevant personnel, activities, and transactions comply, and to achieve the following objectives through the joint efforts of all employees:
(1) Ensure the continuous operation of business activities and the stable use of information services provided.
(2) Ensure the confidentiality, integrity, and availability of information assets, as well as the privacy of personal data.
(3) Establish a continuous plan for information business operations, regularly review and continuously improve the cyber security
management system, and reflect government cyber security management policies, laws, technologies, needs and expectations of
stakeholders, internal and external issues, and the latest status of the Company’s operations. Ensure the feasibility and
effectiveness of cyber security operational practices.
- 2. Review and Implementation of Cyber Security Policy
The Company conducts regular reviews of its cyber security policy each year, collecting and assessing changes in internal and external factors such as organizational, technological, and business aspects, regulations, or the environment. As necessary, revisions are made in a timely manner, and continuous improvement is achieved through the PDCA (Plan-Do-Check-Act) and standardization operations to ensure the ability to maintain effective operations and provide relevant services.
Specific Management Plan
Pou Chen Corporation places great importance on the management and maintenance of cyber security. Building on its existing cyber security protection framework, the Company adheres to relevant regulations and international standards. In 2024, it achieved ISO 27001 international information security management certification (valid from October 12, 2024, to October 12, 2027). The Company will continue to enhance its cyber security capabilities through the planning and implementation of cyber security improvement and optimization projects.
- 1. Policy and Management
Annually, the Company conducts regular reviews to assess whether relevant systems comply with changes in the operating environment and regulatory compliance requirements, and makes timely adjustments as needed. Through continuous cycles of improvement using the PDCA and standardization operations, it aims to achieve sound and effective process control. These operations include:
(1) Regular reviews of information security system
(2) Asset identification and risk management
(3) Continuous operational management
(4) Personnel information security awareness and training
(5) Supply chain information security management
(6) Evaluation of information security effectiveness
- 2. Technology and Protection
To prevent various external information security threats, the Company adopts a multi-layer network architecture design and establishes various information security protection systems to enhance the overall security of the information environment. Operations include:
(1) Network security protection
(2) Endpoint and device security control
(3) Cyber system and application system security mechanisms
(4) Physical and environmental security protection
(5) Data protection mechanisms
(6) Information security monitoring and detection mechanisms
Cyber Security Incident Handling and Reporting
The Company has established an enterprise risk management mechanism and standard procedures for handling information security incidents, clearly specifying relevant processes and measures, including reporting procedures for information security incidents, designation of responsible personnel to handle significant cyber security incidents, and assessing the possible impact of information security risks on the Company’s operations and its corresponding measures.
Impact of Cyber Security Risk Changes on the Company’s Financial or Operations and Countermeasures
In terms of cyber security technology risks and management measures, in addition to structuring the Company's network and information system, the Company has been working closely with supply chain vendors to shorten the relevant information transmission process, effectively improve the operation schedule to enhance operational efficiency, and implement technological management to ensure that it can effectively control the information security risks in the organization and strengthen the information security protection and management mechanism.

